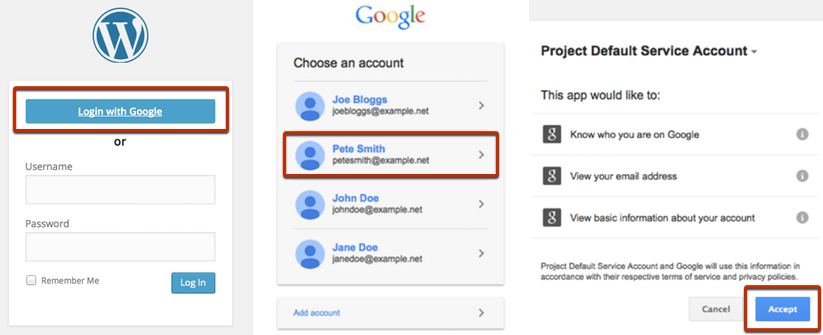
Let’s say you want better security for your WordPress site. Maybe you want your employees to always access their WordPress account by authenticating through Google (which you see as easier than requiring all users to maintain separate usernames/passwords for WordPress as well as Gmail).
You’ve also read about brute force attacks on WordPress, so hope that a Google login will guard against those. You might also have installed a plugin such as Limit Login Attempts to prevent multiple login attempts from the same IP address — likely a sign of a brute force attack (although increasingly such attacks are performed from distributed IPs).
This post explains how to configure Google Apps Login Premium/Enterprise versions to secure your site in this way — and also explains why brute force attacks will never succeed against WordPress when protected by Google Apps Login, so, in fact, your Limit Login Attempts plugin is now completely redundant!
First: What Is a Brute Force Attack?
Brute force attacks are some of the oldest known cyberhacking methods. Today, cybercriminals often rely on computer algorithms to continuously test combinations of usernames and passwords (often known as dictionary attacks) until they find one that works. Although it can be a lot of up-front work for the hacker, it’s still a common method because many people reuse their passwords or create ones that are weak.
In 2017, McAfee Labs published estimates stating that brute force attacks still account for 20% of total network attacks, according to an MIT research paper.
Brute force attacks can have enormous consequences for your WordPress site and your organization as a whole. Hackers often target small teams — and you can suffer staggering financial and repetitional damage in the event of a breach.
The good news is, there are steps you can take to mitigate these threats. Read on to secure your WordPress site.
How Can I Prevent a Brute Force Attack on My WordPress Site?
Taking steps to prevent a brute force attack isn’t hard.
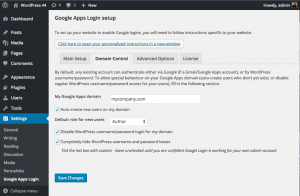
In Settings -> Google Apps Login, click the Domain Control tab and enter your Google Apps domain. Check “Auto-create new users on my domain,” and select a default role.
Once you are happy that at least you as admin are able to “Login with Google” successfully, check the other two boxes on the Domain Control tab:
– Disable WordPress username/password login for my domain
– Completely hide WordPress username and password boxes
Important: Make sure that there are no users in the Users page in WordPress whose emails do not belong to your Google Apps domain and that there are no ways for new users to self-register.
At this point, all your users are required to use Google to log in, and this means that there are no users in existence whose accounts can be brute-force attacked by guessing WordPress passwords. Their WordPress passwords will no longer be usable due to “Disable WordPress username/password login for my domain” being checked. Therefore, Limit Login Attempts is redundant for preventing brute-force attacks.
Since the plugin is simply asking Google “Is this user logged in to their Google account or not” every time a login attempt is made, an attacker can try a million times, but the answer will always be no. The only way for an attacker to impersonate the user is for them to find a way to log in to their Google account first. Of course, Google’s security is much higher by default than WordPress out of the box, especially if you enforce two-factor authentication for all your users — I highly recommend doing that if you think your users will be able to use it.

If you leave Limit Login Attempts active, then of course you may still receive notifications that attacks are being made. It’s entirely possible to still attempt to submit a WordPress username/password, but as outlined above, these will never result in successful logins.
If you are concerned about DoS attacks, then a WordPress plugin won’t help you anyway since such attacks will still overpower your site. Prevention would be required at the web-server level or higher — you’d need to ask your web-hosting company to set this up.
Just to be clear, if “Completely hide WordPress username and password boxes” is checked, then it is still possible to display those boxes (just go to /wp-login.php?gahidewplogin=false) — or, moreover, the end point for a hacker’s script to attempt a WordPress login is still available, even if the boxes themselves were never visible. That’s why it is important to use the “Disable WordPress username/password login for my domain” option, along with the fact that no users outside your Google Apps domain exist on the site.
For more information about configuring the plugin, please see our documentation, or get in touch with any questions!
Please also be aware that other plugins and configurations on your site could mean you still need to take further steps to guarantee security.