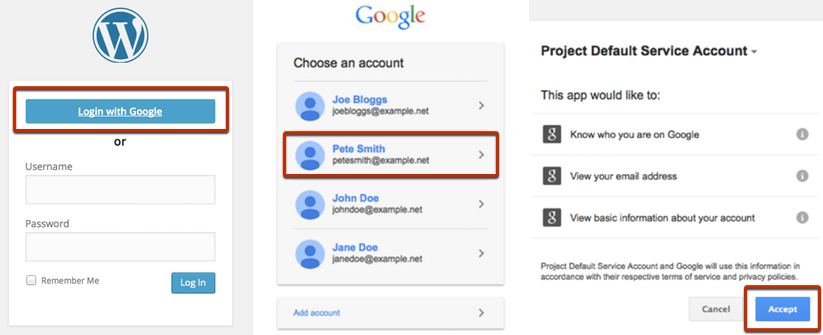
Following a series of Google Apps login phishing attacks (specifically on Google Docs) in 2017, Google made several improvements. At the time, while we welcomed Google taking steps to address the phishing problems, it caused issues for WordPress plugins.
Specifically, the updates made it challenging in cases where customer installation required individuals to create a Google Cloud project with their own OAuth 2.0 Client IDs.
To make things easier and safer for legitimate users who need to create Google applications, we recommended that Google:
- Allow users to authenticate against an OAuth ID they created using the same account as the one being used to access the app.
- Allow admins to whitelist specific ID/Secrets on their domain and also allow any regular Gmail account to whitelist for their own use.
- Provide a simpler verification form, including clear and consistent wording (is a ‘project ID’ the alphanumeric string, or the integer?), plus no long text fields (‘the app needs calendar scopes in order to access the user’s calendar…’). There is no point checking the privacy policy for the app since it can be changed easily in the future and will presumably not be respected by phishers!
- Provide a clearer error message where unverified apps encounter ‘Invalid Scope.’
- Deliver documentation explaining the new verification processes they have rolled out.
- Offer a more robust and selective solution than joining the ‘Risky’ Group (Google already confirmed to us they are aware this cannot be a permanent solution).
Since then, we have even more suggestions for WordPress users using Google Apps login to deter attackers.
Use a Password Manager With Your Google Apps Login
If you don’t opt for Google’s multi-factor authentication (MFA) solution (more on that below), you can still encourage your users to adopt a password management system for extra security.
A recent report by Dashlane revealed that 81% of data breaches are linked to a weak or recycled password. If your users rely on the same password they use for other sites — and especially if it’s an easy-to-guess one like their name, address, or birthday — this has the potential to compromise the back end of your site or company’s intranet.
You can support the use of password managers for your users to help cut down on the risk that a hacker will get their credentials and impersonate them.
PC Mag rated the best password managers of 2018 and came up with the following:
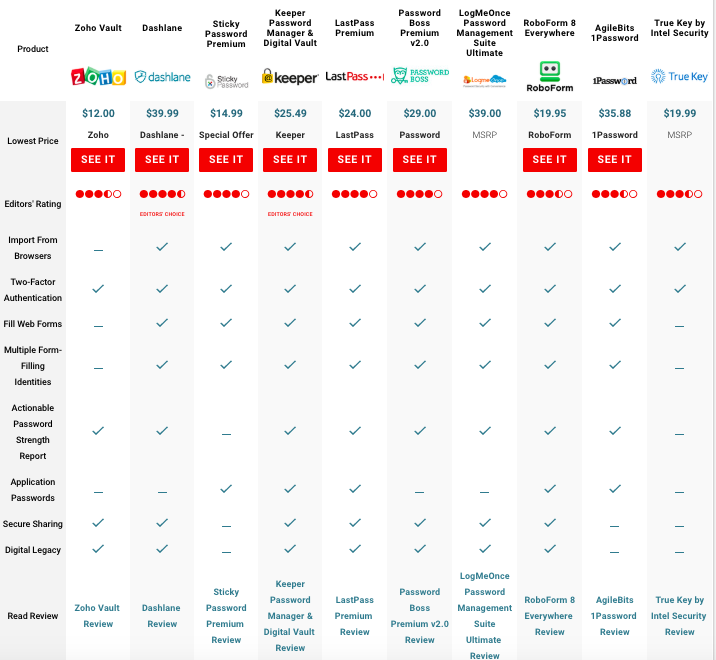
While PC Mag has a host of criteria including price and reviews, the reality is that any of these options is better than simply relying on passwords. Even the more complex ones are possible to breach—and clearly even Google isn’t bulletproof. A password manager offers an extra layer of security between a user and the app or site she’s working with.
Implement Multi-Factor Authentication (MFA)
Multi-factor authentication or MFA takes password precautions to a new level. When you opt for Google login on your WordPress site, you can also choose to use Google’s multi-factor authentication (MFA) solution. Even if a hacker does guess a password — he or she will also have to track down a second piece of identification, such as the user’s phone, to break in.
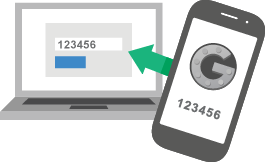
With Google’s two-step verification option, after a WordPress user inputs her credentials, she will also be prompted to send an additional code, sent to her phone via text, voice call, or the Google mobile app. A user can also opt to insert a security key into their computer’s USB port.
A recent study found that more users are opting for MFA over traditional user names and passwords. Adding two-step verification can both help secure your accounts and give your users the experience they’re looking for.
Phishing Attacks Will Continue to Grow
Although Google fixed its Docs vulnerabilities, similar phishing attempts will likely continue to grow.
In 2017, Barkly noted that 76% of organizations experienced phishing attacks. (Source: Wombat 2018 State of the Phish)
In 2018, major phishing scams have unfolded for companies like Mailchimp.
These breaches can take an even more malicious turn. In July 2018, a sextortion scam involved criminals claiming they had recordings of individuals watching porn that they would release if the individuals didn’t send a ransom. In the emails the criminals sent, they included a password they had obtained in a prior data breach.
These scenarios are not out of the realm of possibilities for WordPress users using Google Apps logins. Taking the precautions you need to keep your sensitive data safe will go a long way towards peace of mind and a better overall experience on the site.
If you see anything suspicious, please get in touch with us!